Game Cheat Websites Are Spreading Malware: What Gamers Need to Know
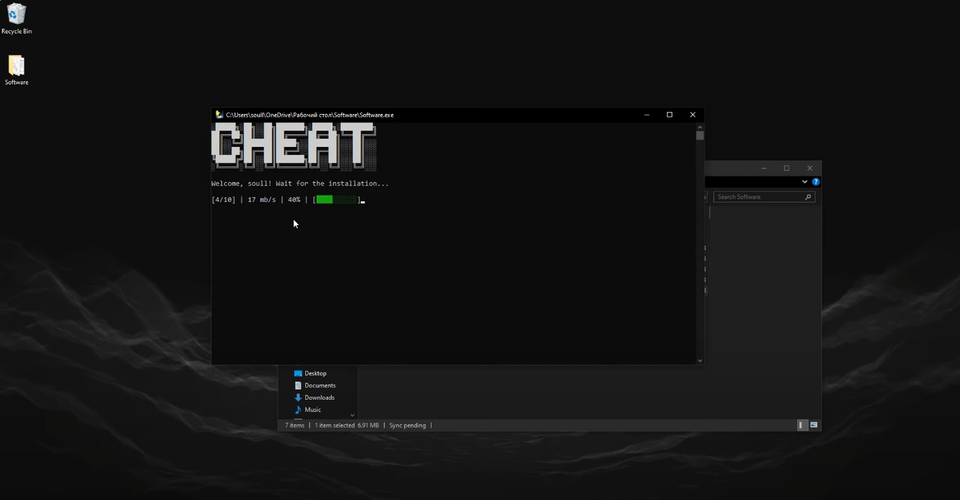
When I first started using computers, like many of my peers in the cyber-security industry one of my earliest introductions involved using cheats to improve my poor aim. This desire to enhance performance is timeless in today's gaming culture, which means threat actors will continue to exploit our vulnerabilities—whether it's the need to impress friends or to boost our kill/death ratio.
In today’s blog, we will analyze a game cheat downloaded from a YouTube video and unravel it's dark side.
IOC's and KQL queries will be included in the post, to help prevent or detect intrusions.
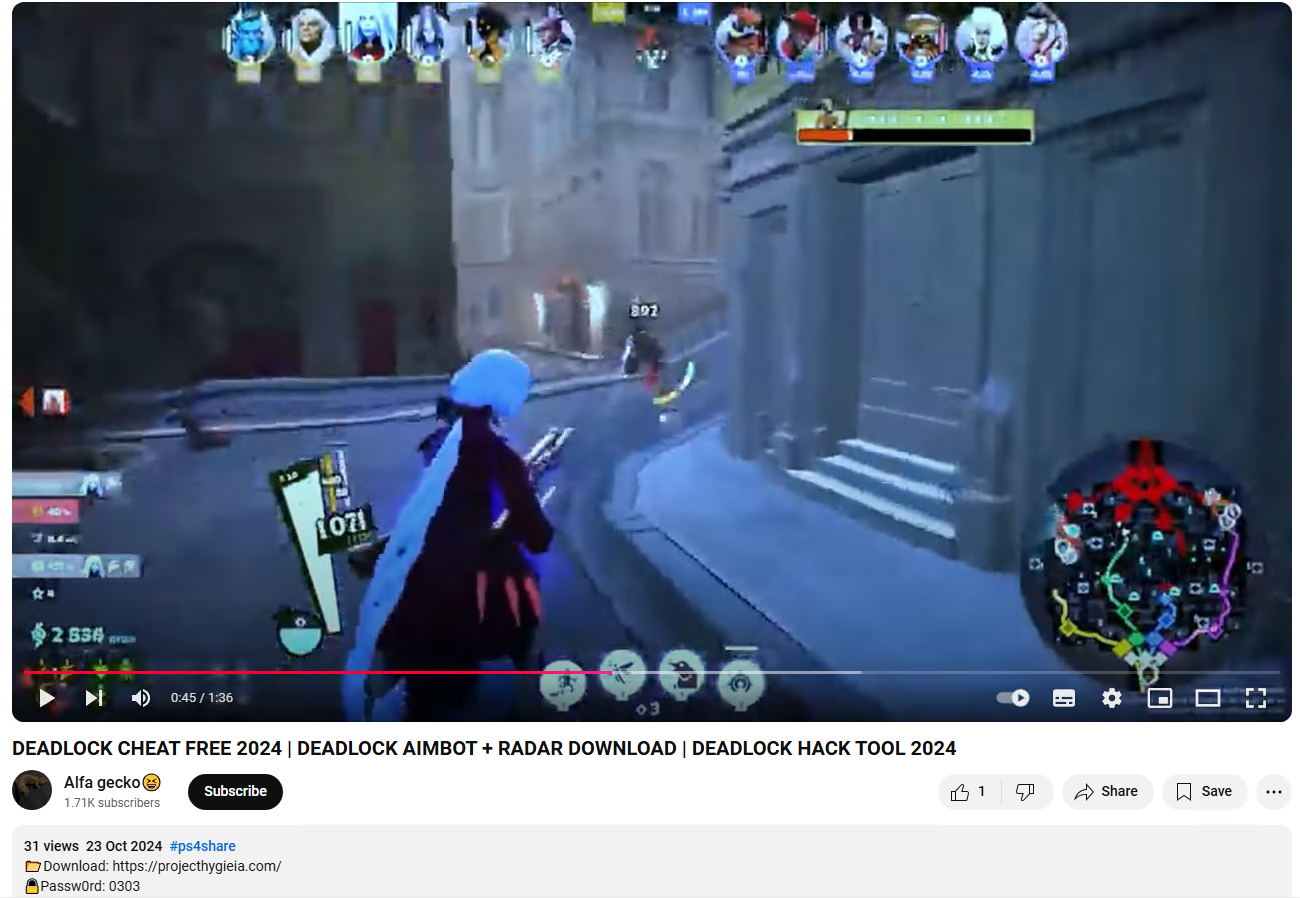
Above is a screenshot of a typical YouTube video promoting a game hack for the newly released game DeadLock.
These accounts are likely compromised YouTube accounts used to further the campaign.
The viewer is instructed to download the "cheat" and follow instructions.
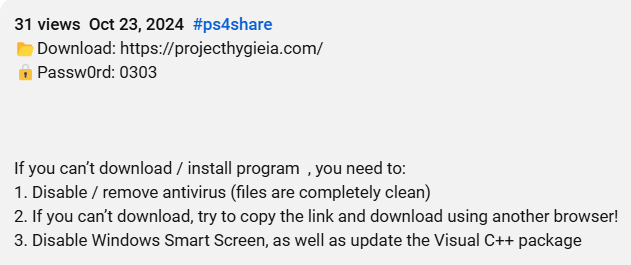
When visiting the listed website, a archive is downloaded to the users browser.
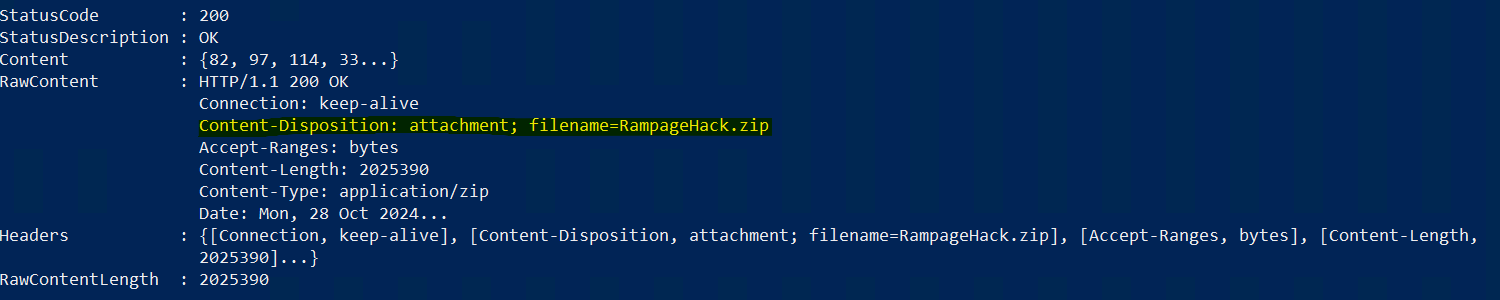
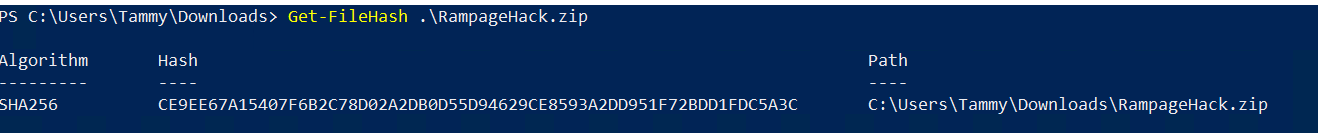
RampageHack.zip:CE9EE67A15407F6B2C78D02A2DB0D55D94629CE8593A2DD951F72BDD1FDC5A3C
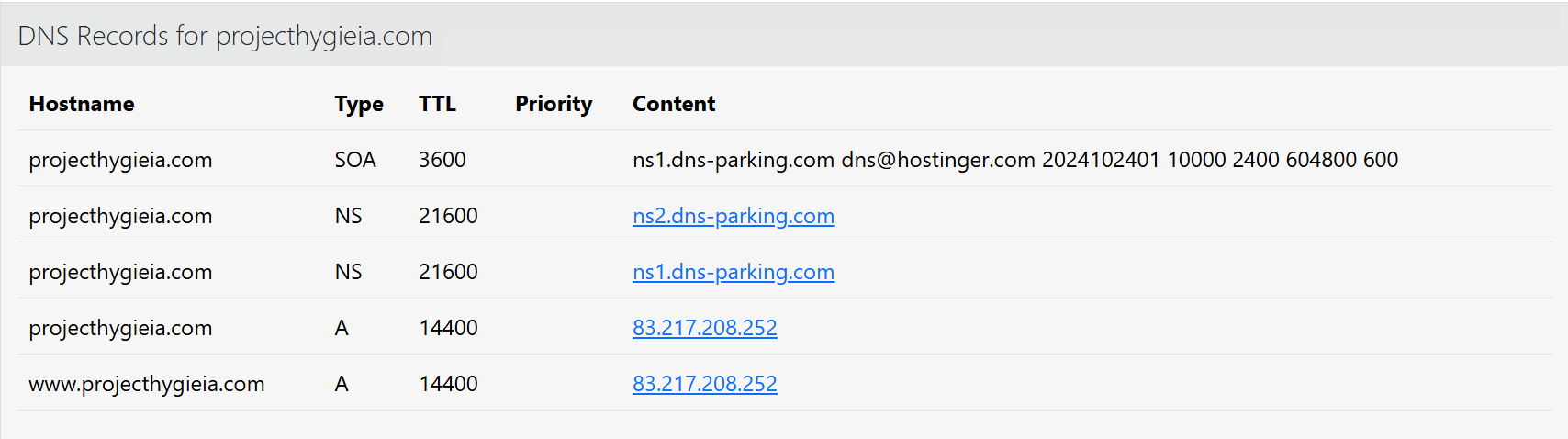
DNS records for projecthygieia[.]com
IP adress report for IOC 83[.]217[.]208[.]252
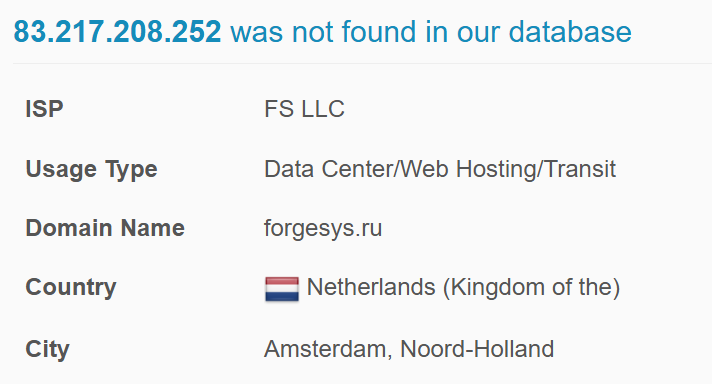
The ISP is a russian registrant forgesys[.]ru take from this what you want 🤨
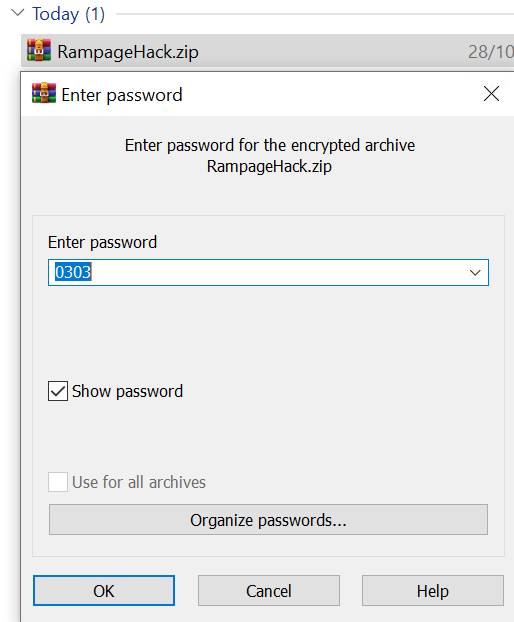
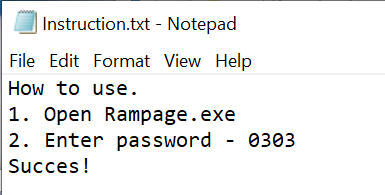
We follow the instructions provided and extract the archive using the passphrase "0303".
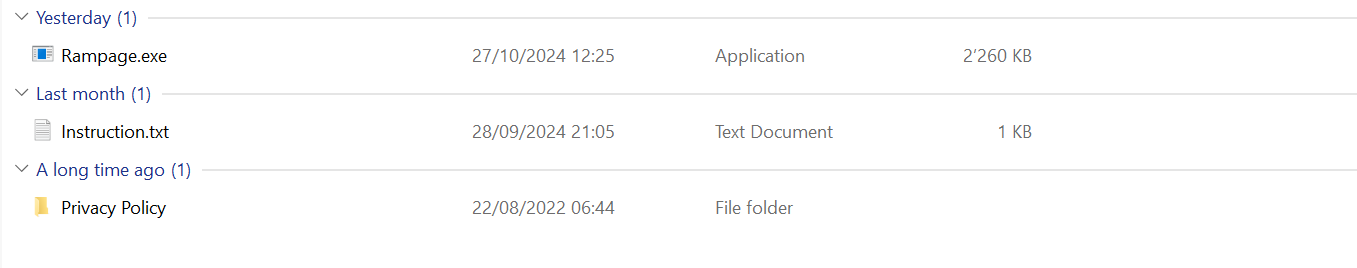
The archive contained one executable, one text file and one folder.
The folder "Privacy Policy" only contains RTF files these are most likely not that interesting.
The text file "Instructions.txt" contains instructions from the author.
The file "Rampage.exe" is an PE file.
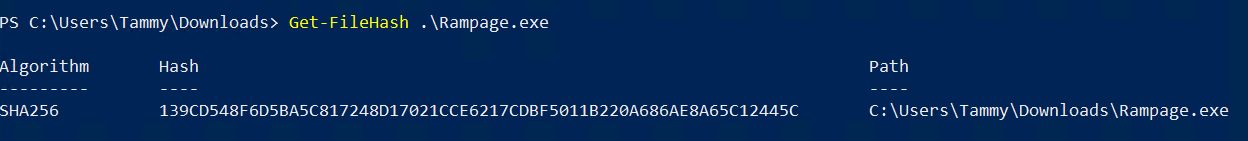
Rampage.exe:139CD548F6D5BA5C817248D17021CCE6217CDBF5011B220A686AE8A65C12445C
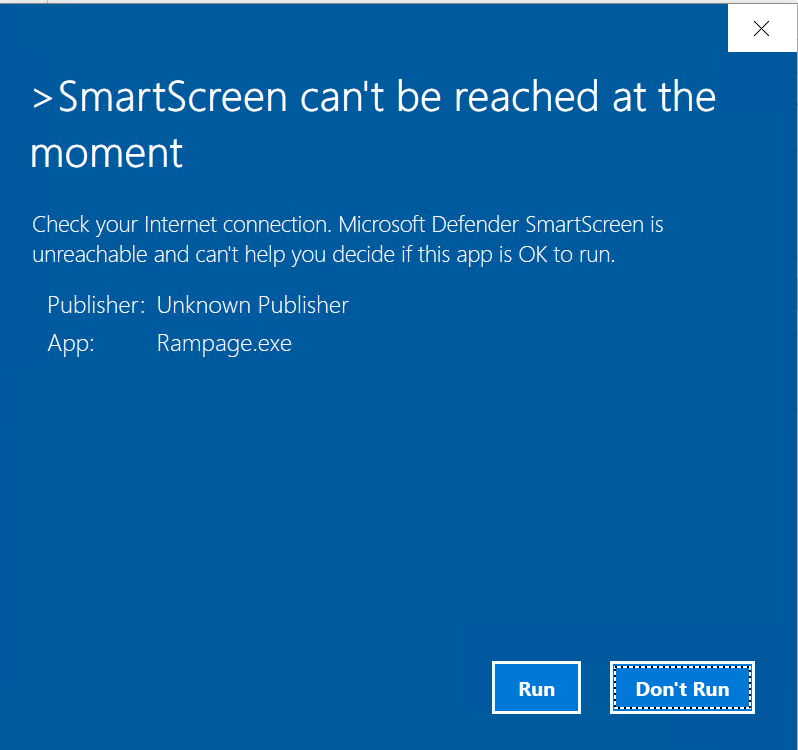
When the executable is ran we are prompted with the SmartScreen.
Bahavioural Analysys
Network activity
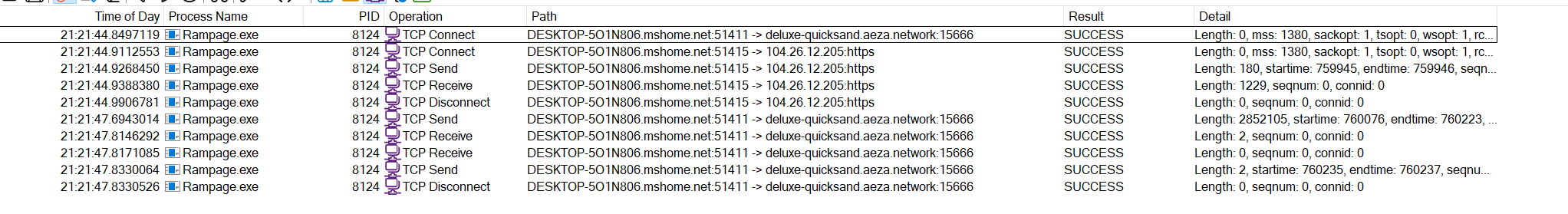
deluxe-quicksand[.]aeza[.]network:15666
104[.]26[.]12[.]205:https
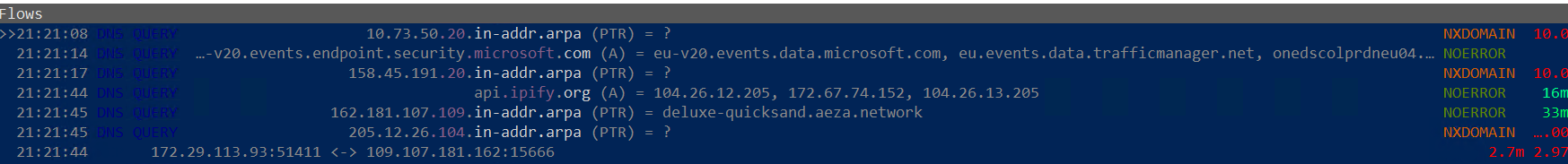
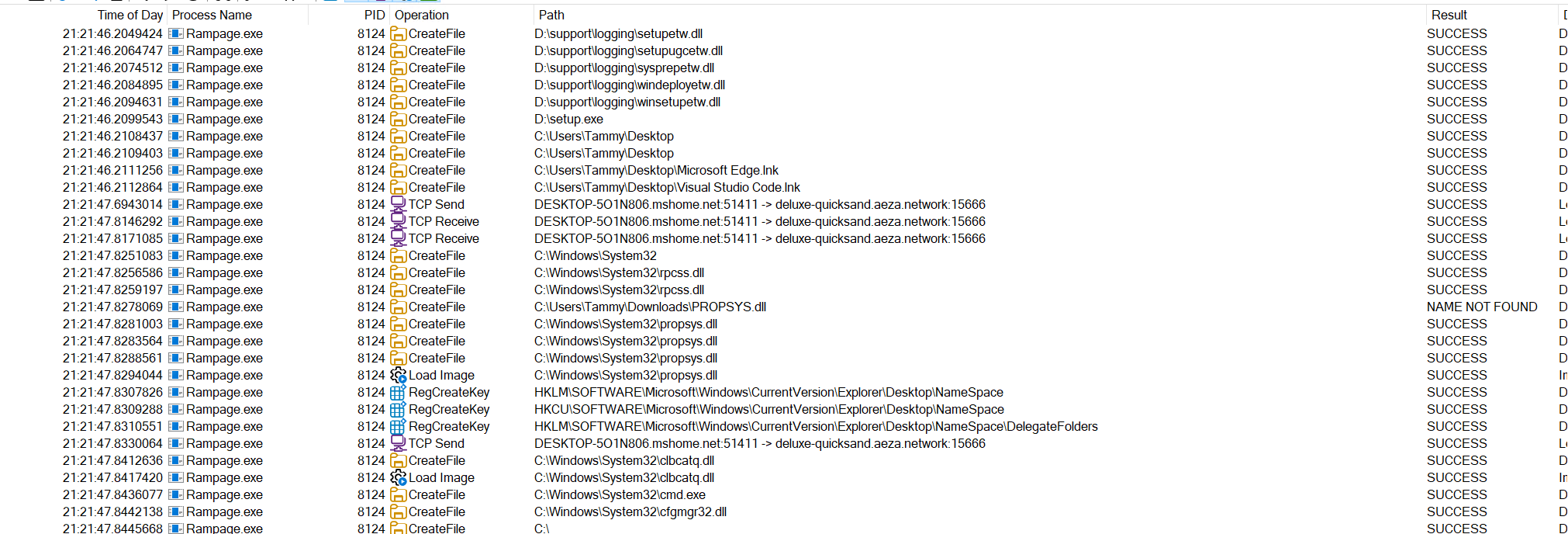
Using filters in procmon we observe what can only be described as information stealing behaviour
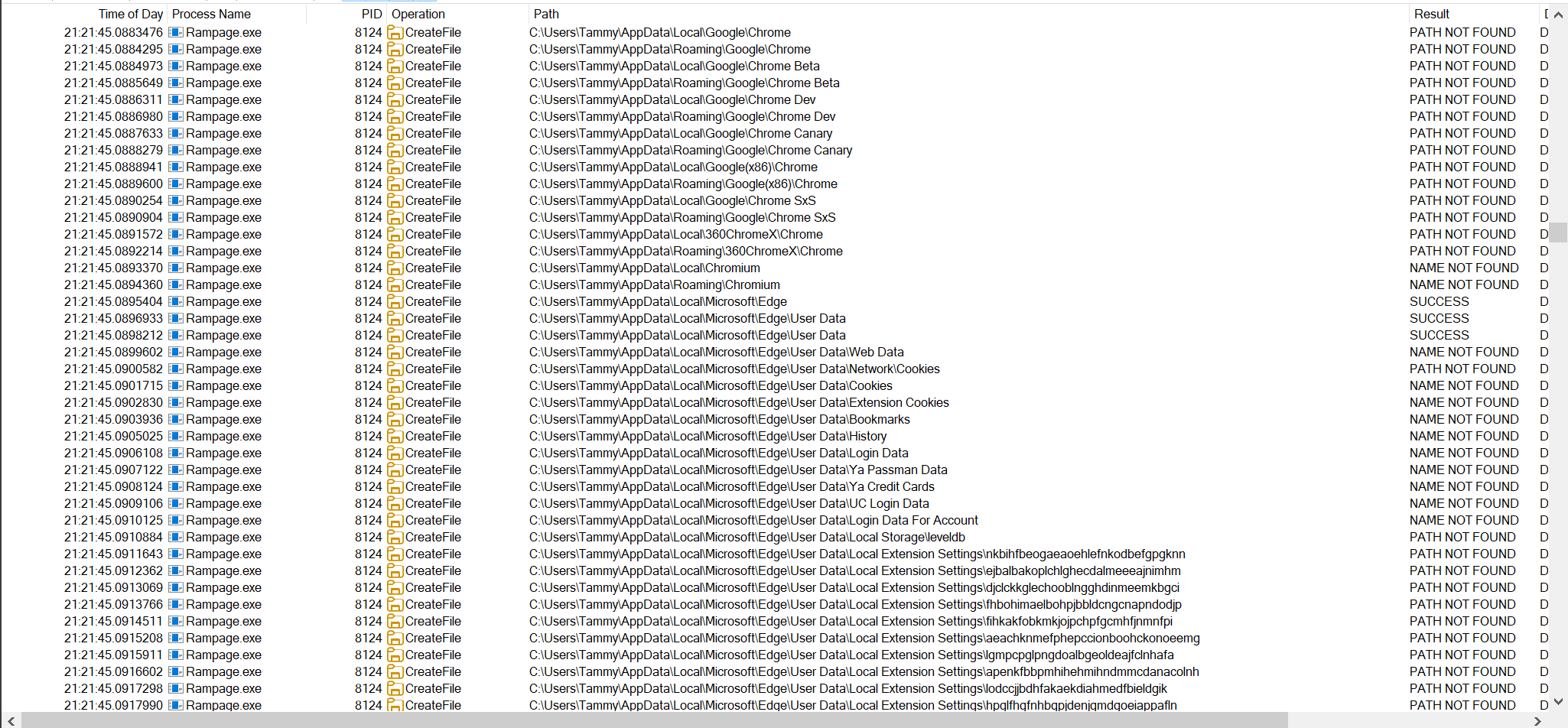
Interestingly the malware is looking for predefined chromium browser extension strings, per example the program is looking for the presence of MetaMask.
C:\Users\Tammy\AppData\Local\Microsoft\Edge\User Data\Local Extension Settings\nkbihfbeogaeaoehlefnkodbefgpgknn

C:\Users\Tammy\AppData\Local\Microsoft\Edge\User Data\Local Extension Settings\ejbalbakoplchlghecdalmeeeajnimhm
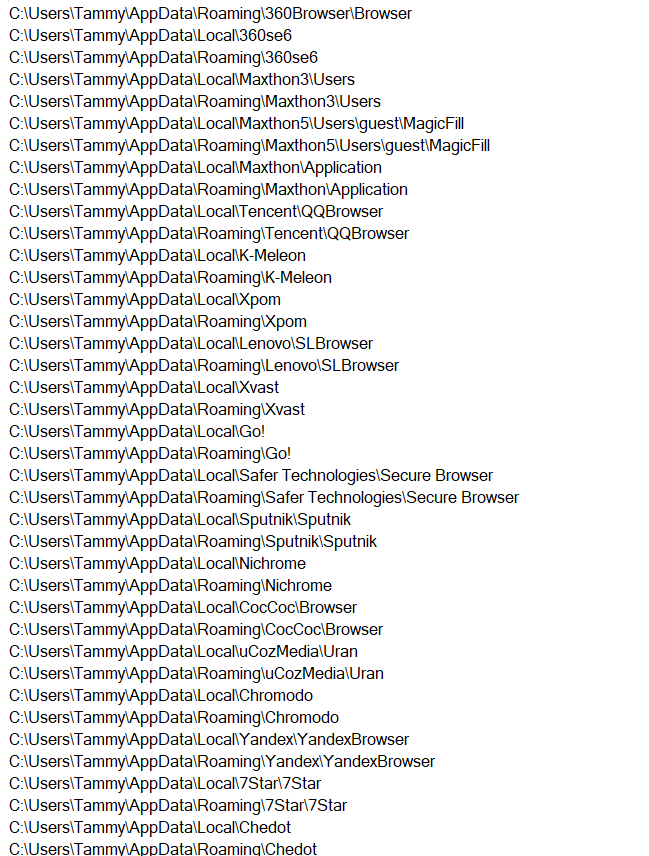
The malware is doing extensive enumeration of existing software
After enumeration of files we can see network and command execution activity, this at first glance would appear as exfiltration activity
To get a better overview of the ongoing activity we will utilize Advanced Hunting as the sandbox is onboarded to defender for endpoint.
KQL Query:
DeviceNetworkEvents
| where DeviceName contains "desktop-5o1n806"
| where InitiatingProcessCommandLine == @"""Rampage.exe"" "
| distinct RemoteIP, RemotePort, Protocol
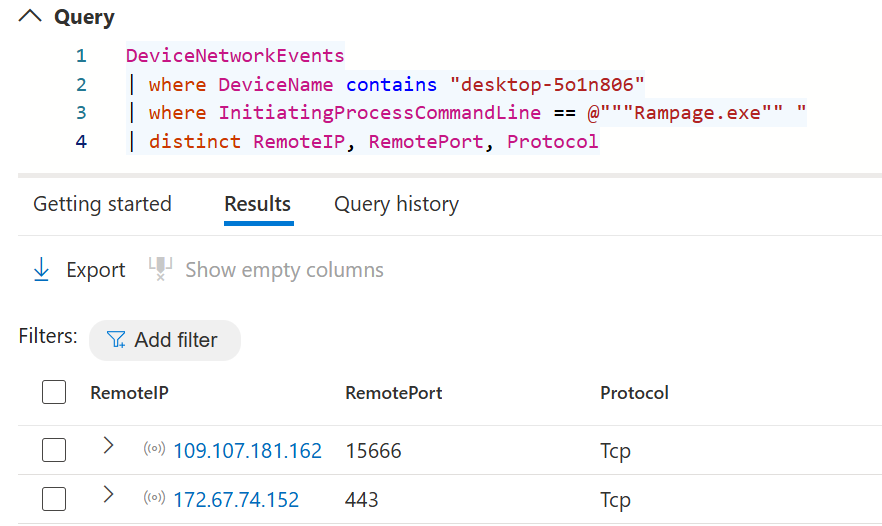
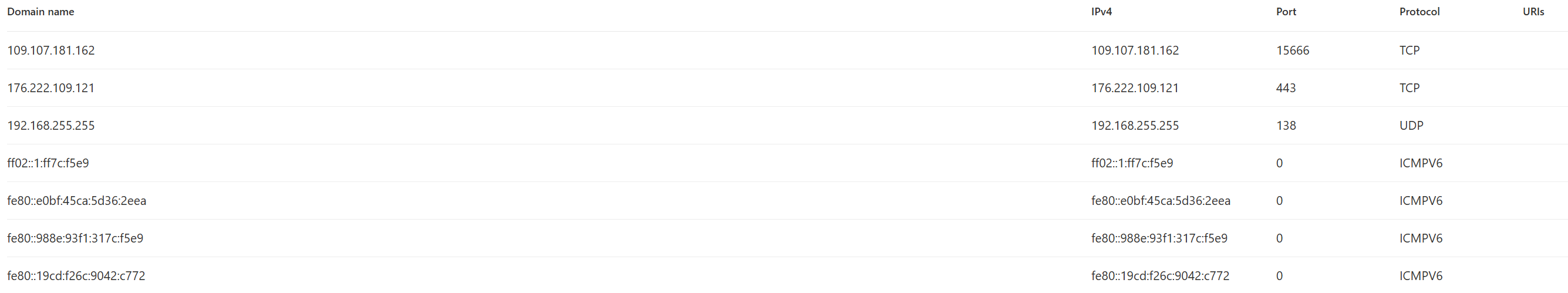
Remote IP's
109[.]107[.]181[.]162 --> port 15666
172[.]67[.]74[.]152 --> port 443
Takes a screenshot:
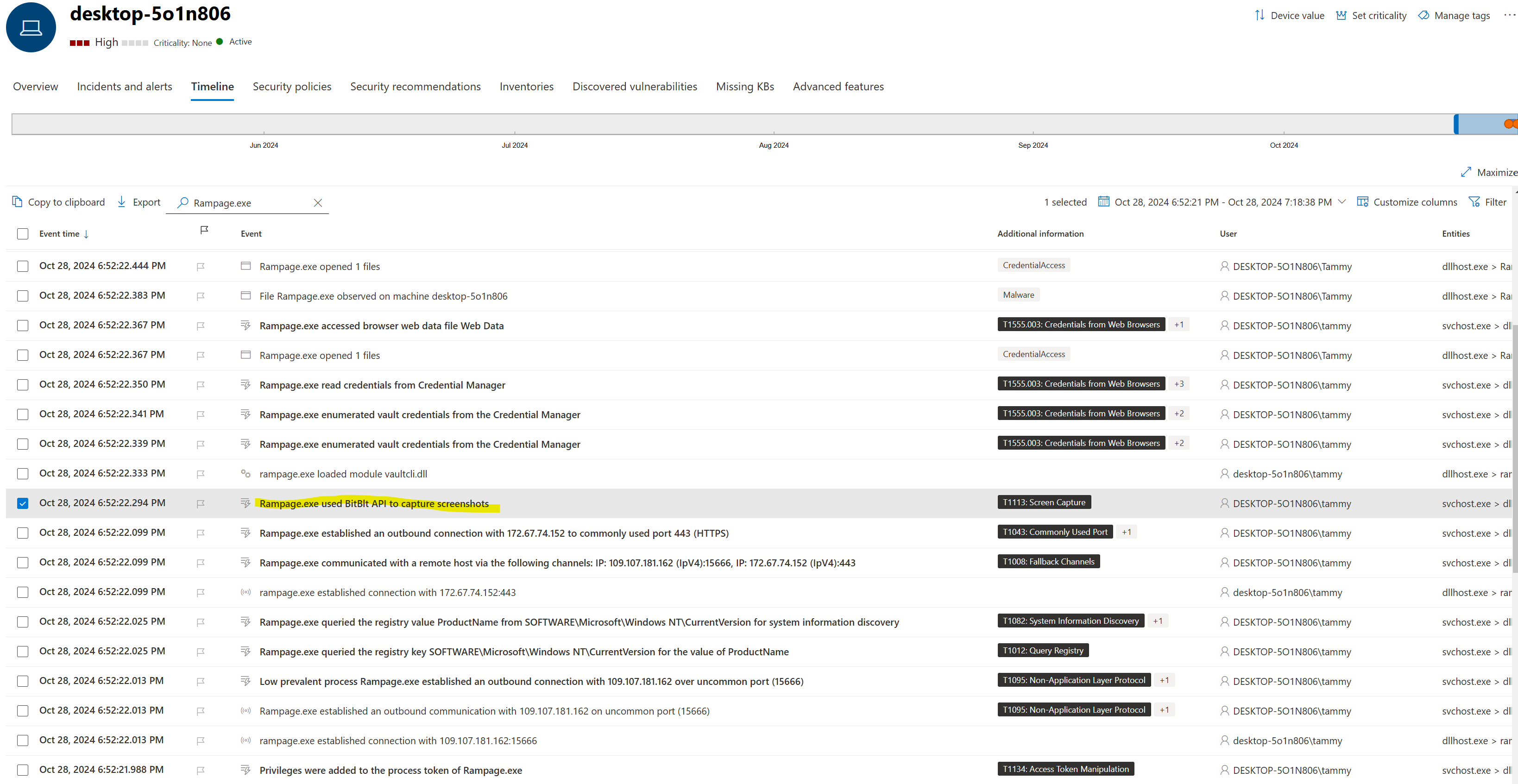
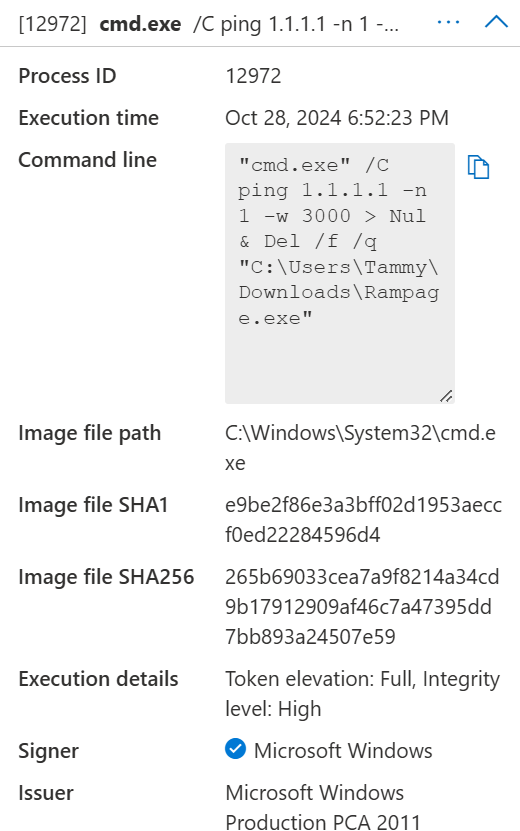
After the data has been collected and sent to the servers hosted by the threat actor, the malware is deleted:
"cmd.exe" /C ping 1.1.1.1 -n 1 -w 3000 > Nul & Del /f /q "C:\Users\Tammy\Downloads\Rampage.exe"
Following the TCP stream directed agains the port 15666 we can observe what looks like base64 encoded data:
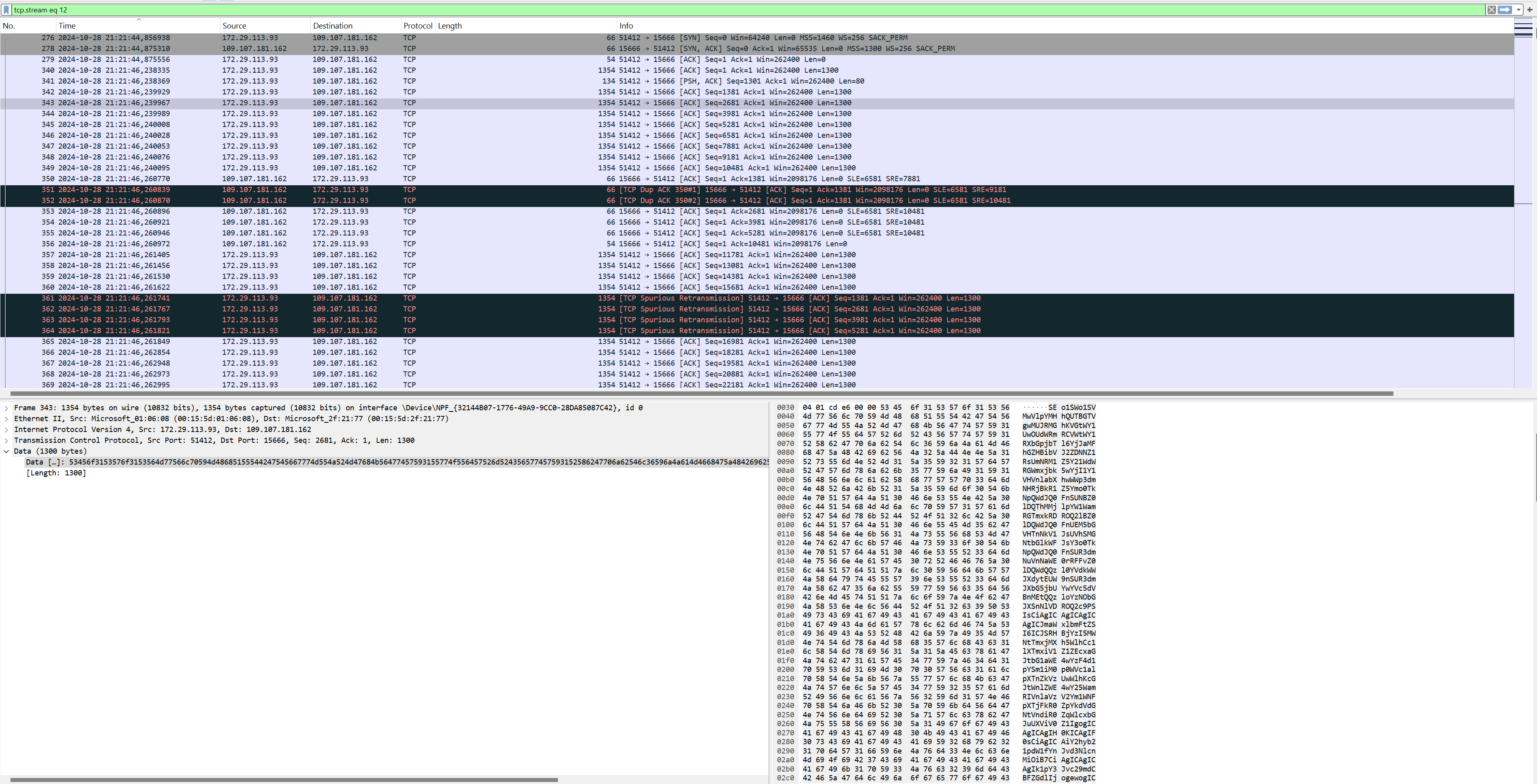
Looking at the stream data we see this more clearly, and what can only be explained as a data/padding pattern:

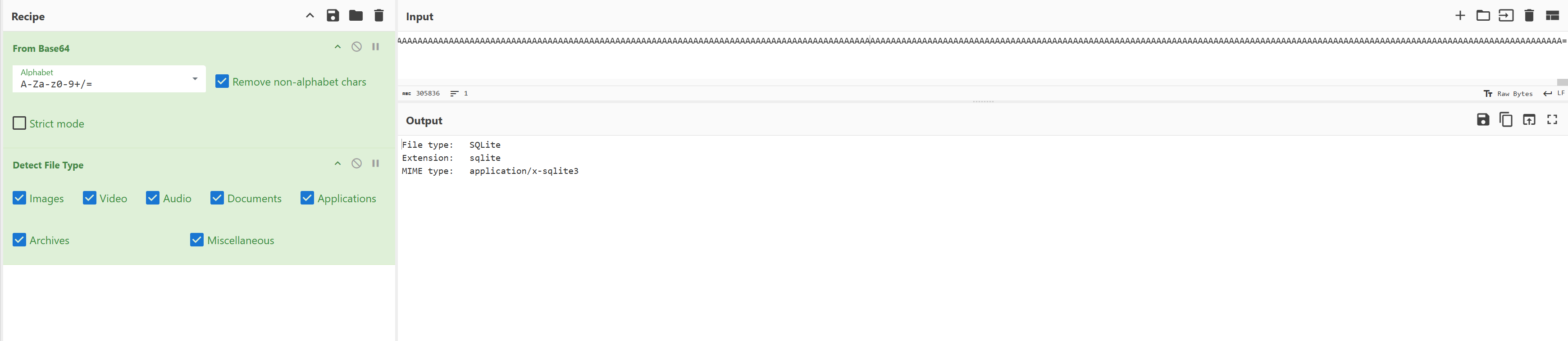
Exporting this data and uploading it to cyberchef and utilizing the base64 recipe will show a complete picture :
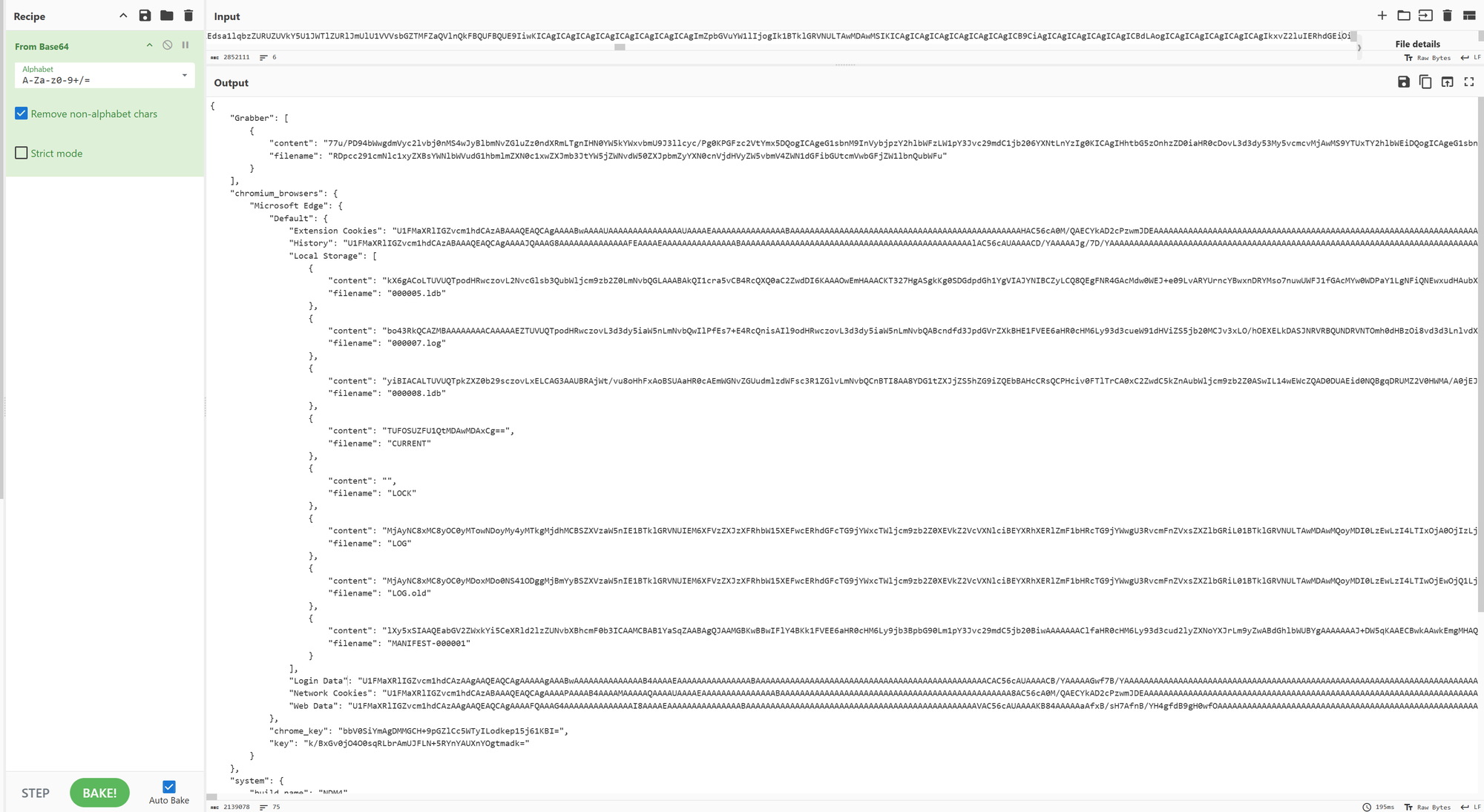
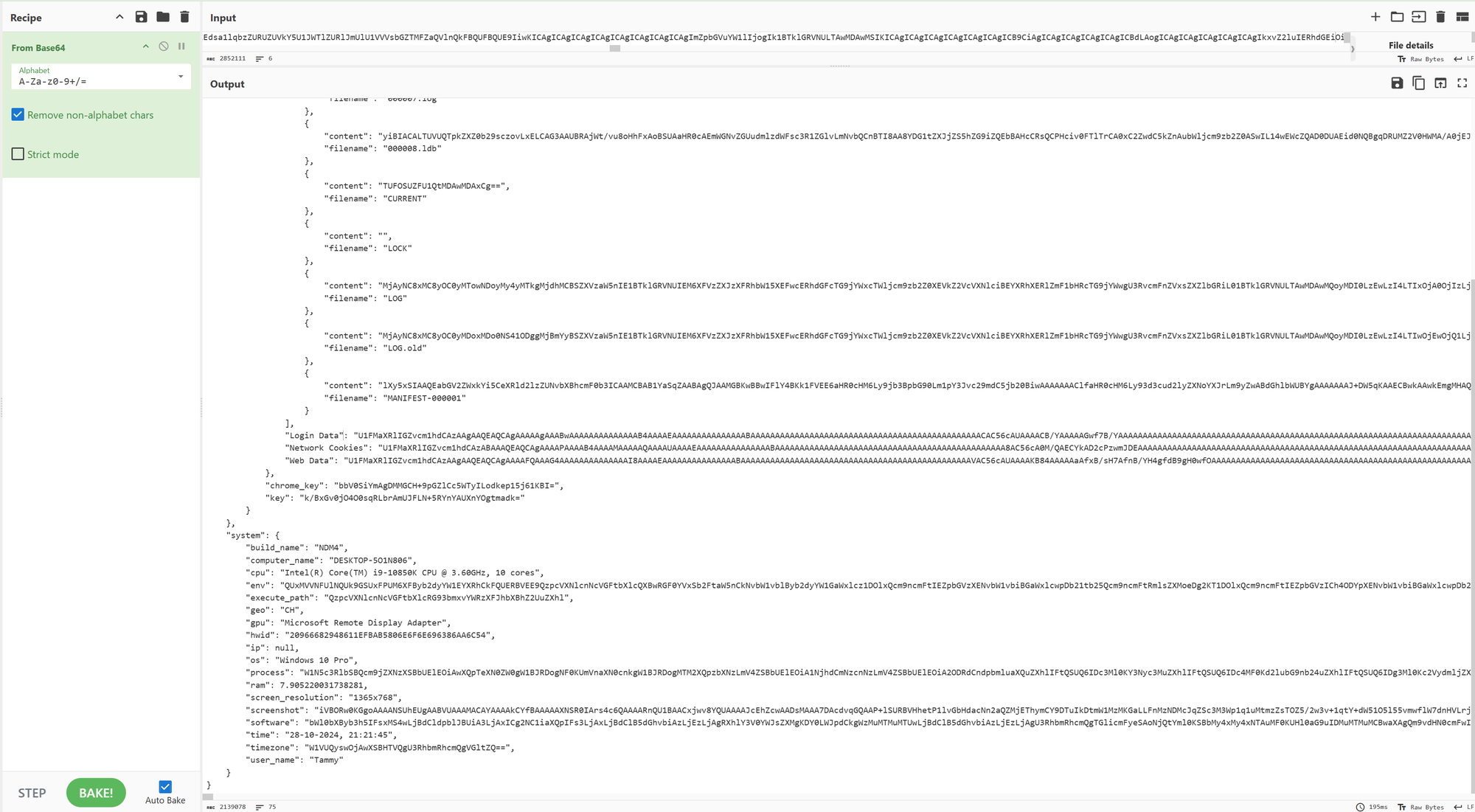
Inspecting this data we can even extract the screenshot that we previously identified the malware taking:
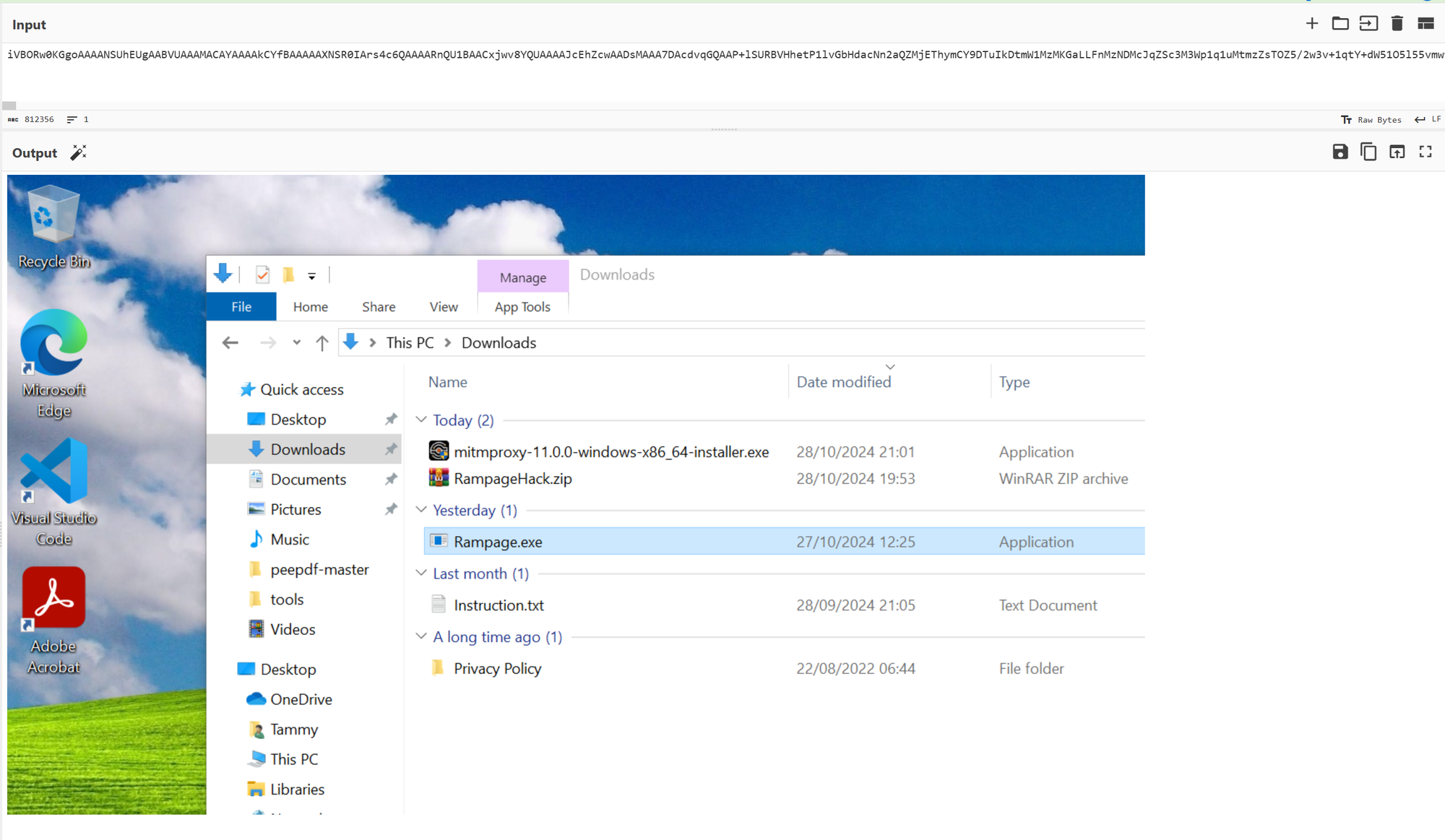
Environment variables:
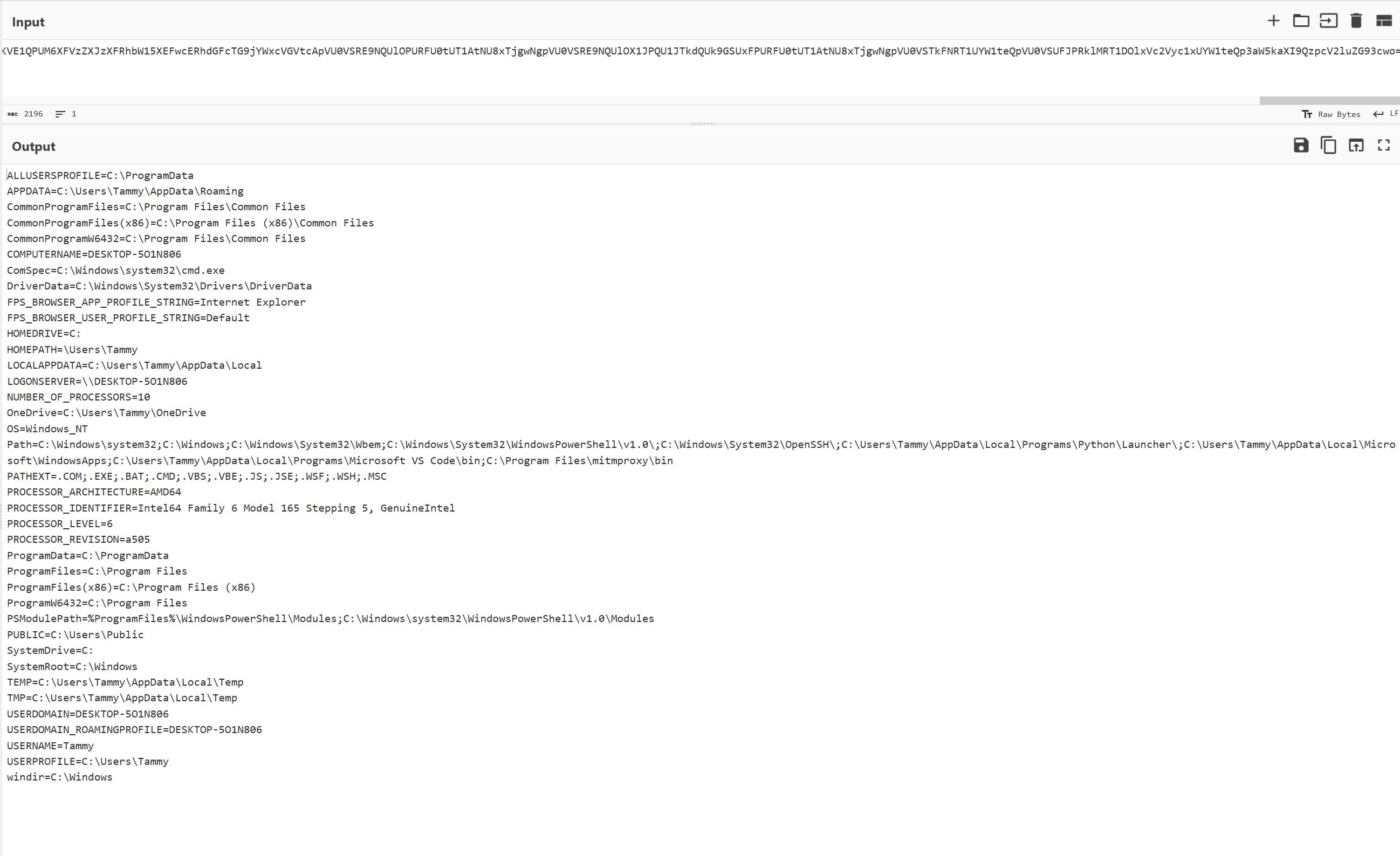
Browser information such as passwords and history is exfiltrated:
The amount of data represented in this data exfiltration will of course differ depending on the data fetched during the enumeration process. But this stealer is deffinetly covering alot of information.
Stealer Portal
Nmap scan report for deluxe-quicksand.aeza.network (109.107.181.162)
Host is up (0.024s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http hypercorn-h11
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
|_http-favicon: Unknown favicon MD5: 52546FCCC0F8DB6A86F70C4D39C6AA9A
|_http-server-header: hypercorn-h11
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=WIN-4NFSE1QOBMS
| Issuer: commonName=WIN-4NFSE1QOBMS
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-08-25T08:06:07
| Not valid after: 2025-02-24T08:06:07
| MD5: 21c7:1e47:d89b:5bb3:9473:bf6a:bc34:9672
|_SHA-1: 502f:b56c:d858:ff23:d1b3:52b9:d0b5:86fe:2644:861e
|ssl-date: 2024-10-28T22:17:09+00:00; -1s from scanner time.
| rdp-ntlm-info:
| Target_Name: WIN-4NFSE1QOBMS
| NetBIOS_Domain_Name: WIN-4NFSE1QOBMS
| NetBIOS_Computer_Name: WIN-4NFSE1QOBMS
| DNS_Domain_Name: WIN-4NFSE1QOBMS
| DNS_Computer_Name: WIN-4NFSE1QOBMS
| Product_Version: 10.0.20348
| System_Time: 2024-10-28T22:16:53+00:00
15666/tcp open unknown
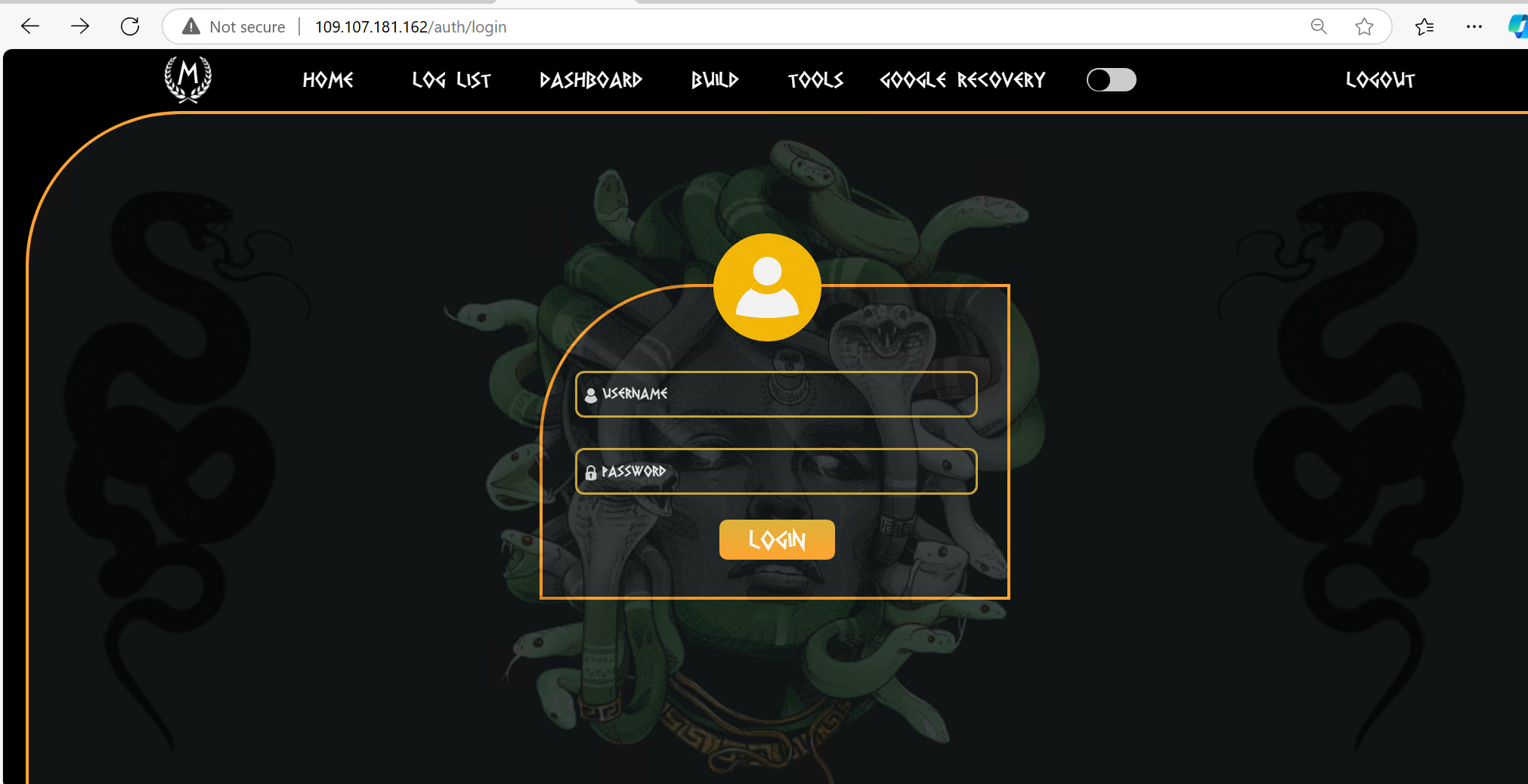
The title of the portal website is "Meduza Stealer 2.15" which gives us a very clear understanding of what type of threat we are dealing with.
Further reading on stealer can be found: https://www.uptycs.com/blog/threat-research-report-team/what-is-meduza-stealer-and-how-does-it-work
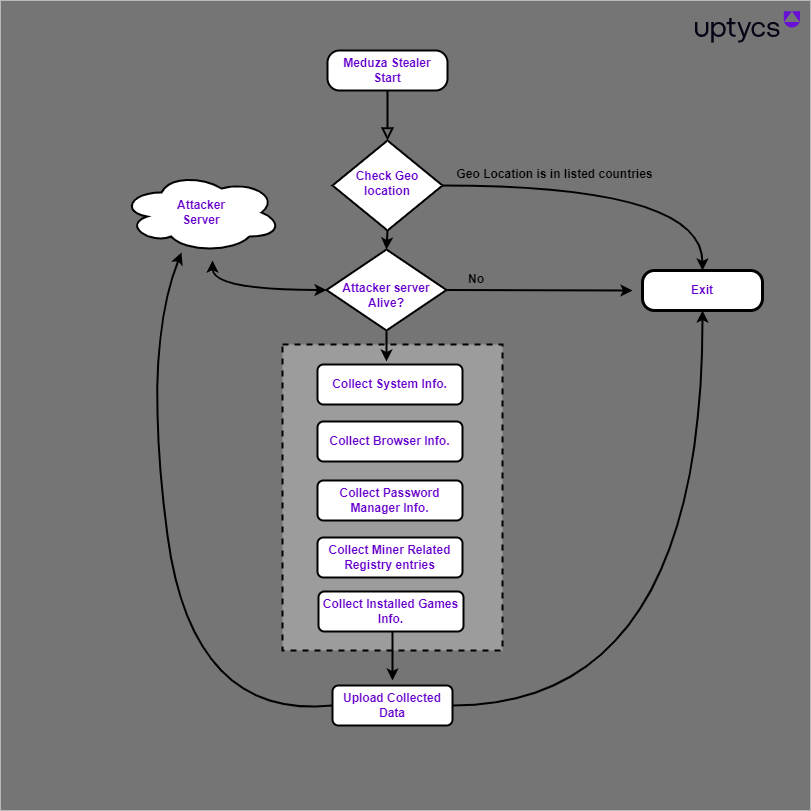
This diagram was found which generally shows stealer process:
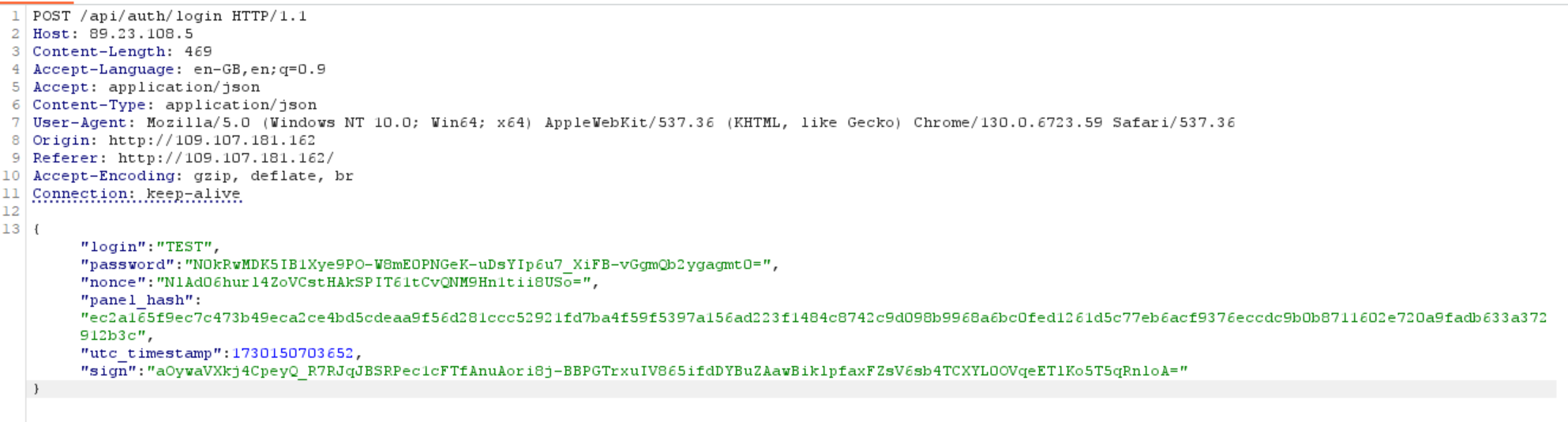
When attempting to sign in on the stealer portal, we observe that the request goes to another server:
89[.]23[.]108[.]5
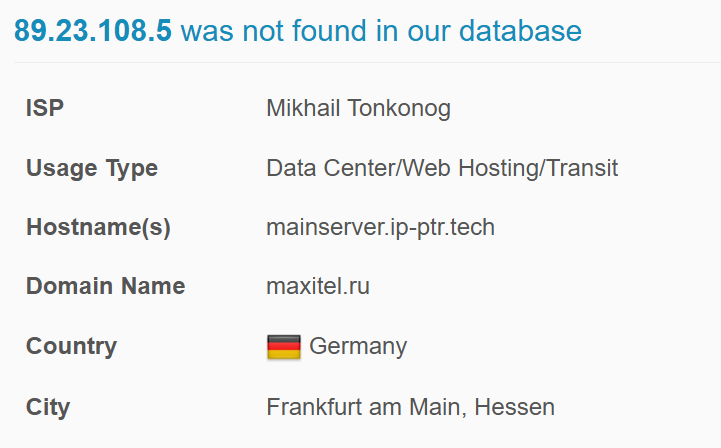
Indicators Of Compromise
|
IOC’s |
|
CE9EE67A15407F6B2C78D02A2DB0D55D94629CE8593A2DD951F72BDD1FDC5A3C |
|
projecthygieia[.]com |
|
83[.]217[.]208[.]252 |
|
139CD548F6D5BA5C817248D17021CCE6217CDBF5011B220A686AE8A65C12445C |
|
deluxe-quicksand[.]aeza[.]network |
|
104[.]26[.]12[.]205 |
|
109[.]107[.]181[.]162 |
|
172[.]67[.]74[.]152 |
|
89[.]23[.]108[.]5 |
KQL Threat Hunt for Meduza Stealer
DeviceProcessEvents
| where ProcessCommandLine contains @"""cmd.exe"" /C ping 1.1.1.1 -n 1 -w 3000 > Nul & Del /f /q"
| where InitiatingProcessSignatureStatus == "Unsigned"
| summarize Process = make_set(InitiatingProcessFileName), InitProcId = make_set(InitiatingProcessId) by DeviceName
DeviceNetworkEvents
| where RemotePort == 15666
| where ActionType == @"ConnectionSuccess"
| where RemoteIPType == @"Public"
| join kind=inner (DeviceProcessEvents) on InitiatingProcessSHA256
| where InitiatingProcessSignatureStatus == @"Unsigned"
Conclusion
As the digital landscape expands and trends like BYOD (Bring Your Own Device) and remote work grow more popular, information-stealing malware is becoming an increasingly effective tool for threat actors seeking access to corporate environments.

Member discussion